Most REST services that are being built using asp.net core now are using token based authentication either using asp.net core authentication middleware or third party products such as Identity Server. But, sometimes you only need to build your APIs for intrenal use within your organization who happens to be using Windows Authentication.
In this point, I will explain how to build a web API that utilizes AD for authentication and AD groups for authorization and how to integrate it with authorization policies.
Creating the project
Open Visual Studio 2017, Create new asp.net core Web Application and name it AspnetCoreWindowsAuth, then press Ok. Choose Web API as a project Template and Change the authentication method to Windows then press Ok to create the project.
If you select the project in the solution explorer and press F4, you will find nothing to set the authentication mode to Windows and enable/disable anonmous access just like you used to do in normal MVC web application. This is because it is moved to the launchsettings.json file under the properties folder. If you want to change it, you have to open the file and edit the value of the json property iisSettings which looks like below:
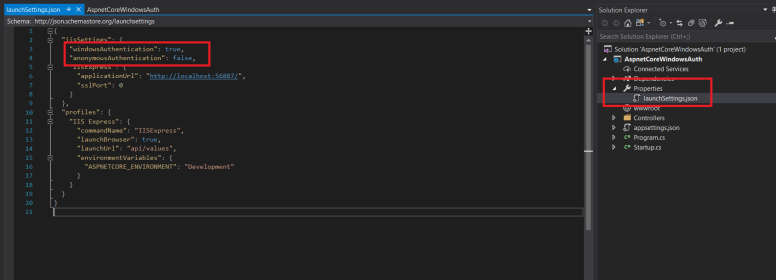 You can also modify the URL and SSL settings.
You can also modify the URL and SSL settings.
Now, if you run the project, it will run just fine and you can call the default Values controller and see the output and even windows authentication will be working as well and you can get the name of the logged in user using the User.Identity.Name property and it will return the Domain\\username although we didn’t add any authentication code yet in the pipeline
Add windows authentication middleware
Now, lets add the authentication middleware into the request processing pipeline. Add the line app.UseAuthentication(); in the Configure method just before the app.UseMvc(); . Remeber that the middlewares run in the same order they were added in the Configure method.
Add the following code in the ConfigureServices method before the services.AddMvc();
services.Configure(options =>
{
options.AutomaticAuthentication = true;
});
services.AddAuthentication(IISDefaults.AuthenticationScheme);
To make sure this is working fine, you can edit the Authorize attribute on the ValuesController and add the role name which should be an AD group name, ex: Employees
[Authorize(Roles ="Employees")]
Now you have asp.net core working fine with Active Directory and you can can authenticate the users according to the AD groups they belong to.
Using Authorization Policies
If you need more fine grained control over your controllers and you need to add more authorizastion logc, then you can go for authorization policies and it is really easy to configure as you can see below. Just add the following lines in the ConfigureServices method before the AddMvc statement
services.AddAuthorization(options =>
{
options.AddPolicy("OnlyEmployees", policy =>
{
policy.AddAuthenticationSchemes(IISDefaults.AuthenticationScheme);
policy.RequireRole(""S-1-5-4");
});
});
Here we defined a policy called OnlyEmployees and it requires the users to be windows authenticated and in the Role named Employees which is eventually mapped to AD group named employees. Notice that I didn’t write the name Employees in the RequireRole method. Instead, the value “S-15-4” was used, which is the SID for the AD Group named Employees. I found that this is how the group names are mapped to Roles in asp.net core and even if you tried to retrive the list of claims that the user have, it will translate to all SIDs of the groups that the user belongs to in AD.
To utilize this policy you have to annotate the controller or method with it as below
[Authorize(Policy = "OnlyEmployees")]
[Route("api/[controller]")]
public class ValuesController : Controller
{
}
By now you should have a working solution that depends on windows authentication and AD groups. Notice that this will only work with windows and most probably IIS.
You can find the code on GitHub if you want to use it or add to it.
